API Feature
Security
Role-Based Access Control
Define custom roles, assign granular permissions, and control access at the resource level.
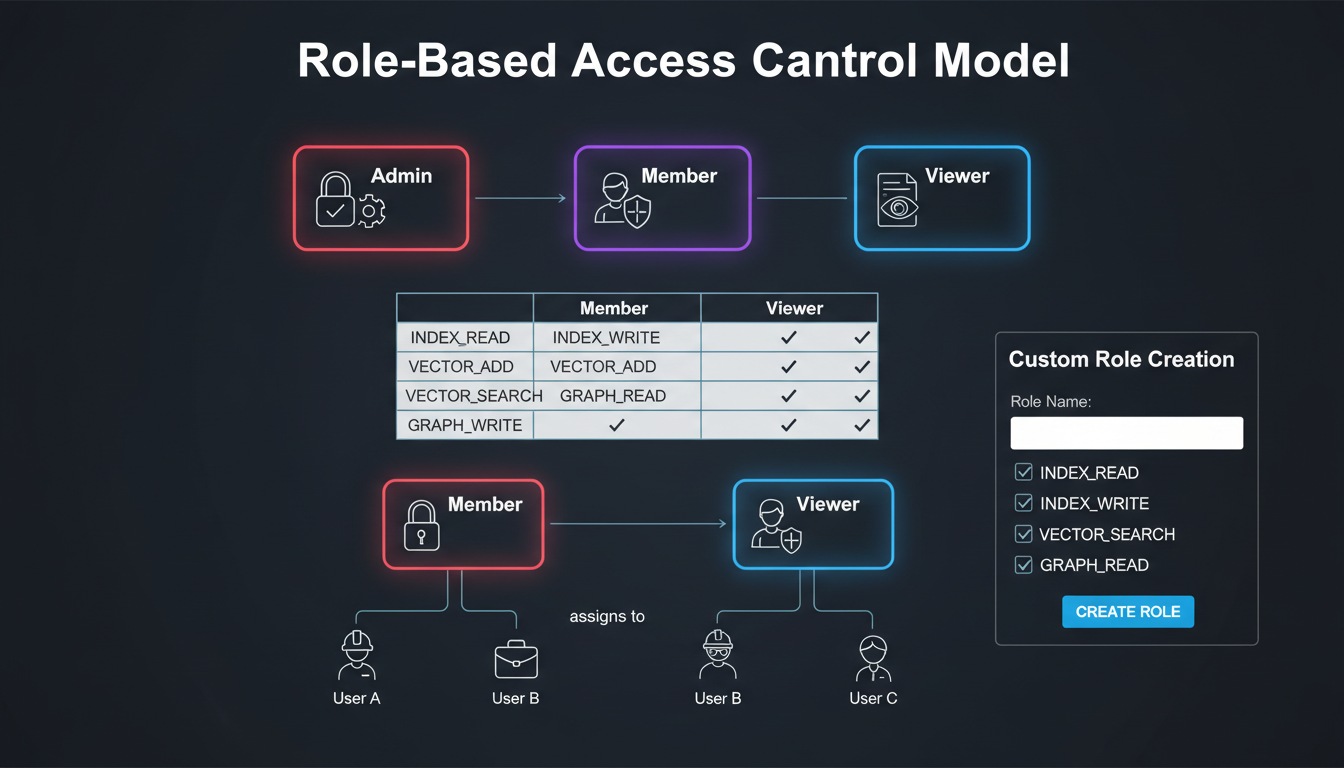
Role hierarchy with permission inheritance
Permission Model
MLGraph uses a resource-action permission model. Permissions follow the formatresource:actionand can include wildcards.
Resources
- • indexes
- • vectors
- • search
- • users
- • roles
- • apikeys
- • audit
- • settings
Actions
- • read
- • write
- • delete
- • admin
- • execute (for search)
- • * (all actions)
Built-in Roles
| Role | Permissions |
|---|---|
| owner | *:* |
| admin | indexes:*, vectors:*, search:*, users:*, roles:read, apikeys:*, settings:* |
| developer | indexes:*, vectors:*, search:execute, apikeys:read |
| analyst | indexes:read, vectors:read, search:execute |
| viewer | indexes:read, vectors:read |
Custom Roles
// Create a custom role
POST /api/roles
{
"name": "ml-engineer",
"description": "Can manage indexes and run searches",
"permissions": [
"indexes:read",
"indexes:write",
"vectors:write",
"search:execute"
],
"inherits": ["viewer"] // Optional inheritance
}
// Assign role to user
POST /api/users/user-123/roles
{
"roleId": "ml-engineer",
"scope": {
"type": "index",
"resources": ["production-*"] // Wildcard pattern
}
}
// Check permission
GET /api/auth/check?
permission=indexes:write&
resource=production-vectors
// Response
{
"allowed": true,
"reason": "role:ml-engineer grants indexes:write on production-*"
}Resource-Level Access
Permissions can be scoped to specific resources using patterns:
indexes:read:production-*Read any index starting with "production-"
vectors:write:user-${userId}-*Write to user's own indexes (dynamic)
search:execute:*Search any index
Permission Inheritance
Inheritance Rules
- • Roles can inherit from other roles
- • User permissions = union of all assigned roles
- • More specific permissions override inherited ones
- • Explicit deny overrides all allows
- • API key permissions are a subset of user permissions